Email providers such as Google now require sending domain names to have SPF, DKIM, and DMARC records within their DNS settings for authentication purposes. Failing to do so may result in your messages bouncing if you are a high volume sender. We’ve provided a brief guideline below on DMARC and how you can construct your own DMARC record. We recommend you familiarize yourself with it, but you can also skip to the ‘Short Version’ section at the end for a quick resolution if your email is already bouncing.
DMARC (Domain-based Message Authentication, Reporting & Conformance) is an email authentication policy and reporting protocol used on top of the SPF and DKIM protocols. Fundamentally, it specifies what to do with email that fails SPF and DKIM checks, and it adds a level of “alignment” ensuring that domains and/or email addresses line up so what the receiver sees matches the envelope and technical details.
Alignment requires that the technical information used to check SPF and DKIM matches what the user sees in the FROM header shown in the email message, and can be specified as either strict or relaxed. SPF alignment requires the RETURN PATH header, also called the “envelope FROM”, to match the message FROM header which the end uses sees when he/she reads the email, with relaxed alignment only the domain name part of the email addresses must match, while with strict alignment the addresses must match in their entirety. For DKIM alignment, the domain indicated in the d= field of the DKIM record is required to match the domain from the message FROM header, with strict alignment, meaning the match must be exact, while relaxed allows for d= to be a subdomain of the from the domain.
DMARC specification allows for the fact that email-sending infrastructure can be complex and that for an organization to implement this all at once could result in lost email due to several causes, including 3rd party providers with different configurations. It includes several methods for gradually implementing DMARC, so that organizations can ease into full deployment over time.
To implement DMARC safely, it is best to follow the steps below:
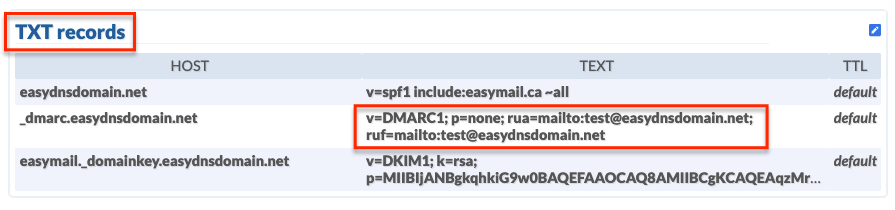
DMARC records need to be created under the hostname _dmarc.example.com, and consist of a TXT record including some or all of the following fields.
Tag Description Example
A typical DMARC record might look like
“v=DMARC1;p=reject;pct=50;rua=mailto:postmaster@example.com”
This would indicate that 50% of DMARC failures should be bounced, and the aggregate reports should be sent to postmaster@example.com.
SHORT VERSION
DMARC (Domain-based Message Authentication, Reporting & Conformance) is an email authentication policy and is used on top of SPF and DKIM records. To implement DMARC you’ll need to do the following:
HOST
_dmarc.yourdomain.com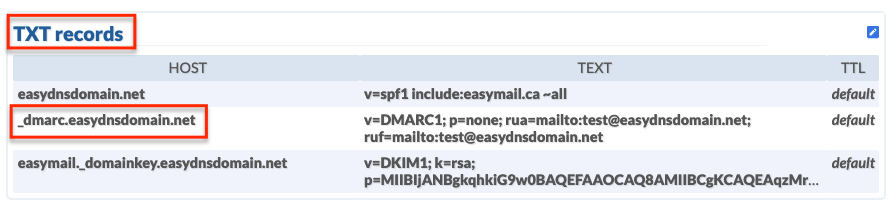
VALUE
v=DMARC1; p=none; rua=mailto:you@youremail.com; ruf=mailto:address@example.com